Our expert in cyber security can offer wide ranges of experiences and provide support for critical problems. Contact us for more details.
Project 1
Title: Enhancing Organizational Resilience through ISMS Risk Management: A Scenario-Based Analysis
Description:
This work investigates into the critical role of Information Security Management Systems (ISMS) in fortifying organizations against evolving cyber threats. Through a scenario-driven approach, it demonstrates the practical application of ISMS risk management, emphasizing the significance of tailored risk assessment, mitigation strategies, and continuous improvement. Using a multinational financial corporation as a case study, the analysis showcases how ISMS protocols can effectively safeguard sensitive data and mitigate financial and reputational risks.
Softwares/Tools:
The project likely utilized standard research tools and methodologies for scenario analysis, risk assessment, and ISMS implementation.
Specific tools could include industry-standard frameworks for ISMS implementation such as ISO/IEC 27001.

Project 2
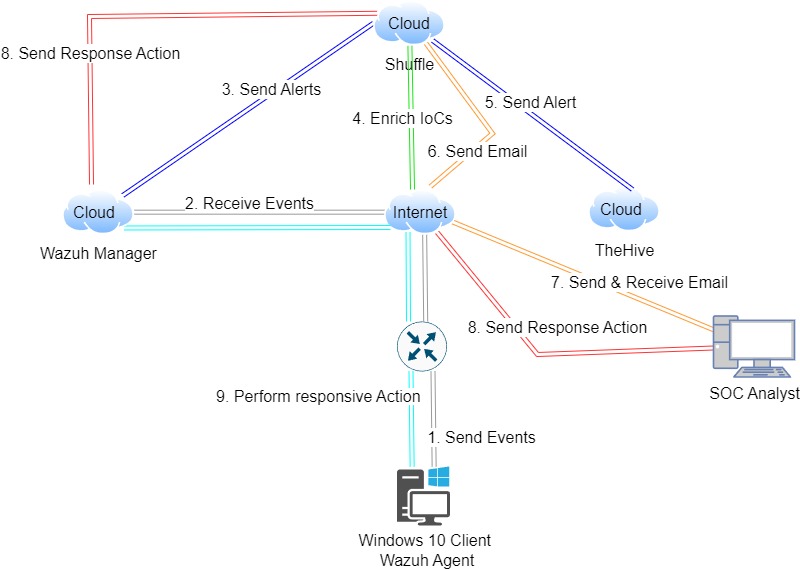
Title: Building an Automated SOC Ecosystem: A Seamless Workflow for Threat Detection and Response
Description:
This project outlines a comprehensive approach to building a Security Operations Center (SOC) ecosystem for efficient threat detection and response. Utilizing Wazuh, Shuffle, and TheHive, the workflow seamlessly integrates various components to automate security incident handling. From event collection on Windows 10 PCs to response orchestration via email communication, each component plays a crucial role in streamlining the SOC workflow. By automating responses to security threats, organizations can bolster their cybersecurity posture, reduce manual intervention, and enhance overall incident response capabilities.
Softwares/Tools:
Wazuh for event collection,
Shuffle for alert enrichment, and
TheHive for incident response and case management.
Additionally, standard tools and techniques for email communication, virtualization (e.g., Virtual Machines), and cloud-based infrastructure (digital ocean) were likely utilized.

Project 3
Title: Fortifying Healthcare: A Comprehensive Security Framework for Hospital Information Systems
Description:
This work introduces a robust security framework for Hospital Information Systems (HIS) to address evolving threats in healthcare. Using 5G communication and Docker containers, it emphasizes threat modeling, attack scenarios, and countermeasures. The framework ensures confidentiality, integrity, and availability of sensitive medical data, exemplified through simulations of medical devices and web applications. Techniques include network monitoring, anomaly detection, and container security best practices. The study advocates for continuous monitoring and adaptive security measures in 5G-enabled medical networks to safeguard patient data.
Softwares/Tools:
Docker Swarm,
Visualizer ( docker-swarm-visualizer )
DICOM protocol, Flask,
STRIDE framework,
Network monitoring tools (Wireshark, Suricata, Snort), Elasticsearch with Elastic Stack, container security tools (Clair, Anchore, Twistlock),
CI/CD pipeline integration,
Encrypt for certificate management, Security Information and Event Management (SIEM) solutions, Docker Security Scanning, and incident response planning.


